Encrypting Ransomware is a category of malware that infects your computer (yes, even Macs) in a way that it encrypts your files and uploads the decryption key to the attackers. This way, you have to pay a ransom in order to, allegedly, get the encryption key back. Of course, you have no guarantee that you will be given the decryption key back. Ransomware typically propagates as a trojan, whose payload is disguised as a seemingly legitimate file. Some notorious examples are:
- CryptoLocker - first seen September 2013
- CryptoLocker.F and TorrentLocker - first seen September 2014
- CryptoWall - first seen September 2014
- KeRanger - first seen March 2016 and is the first one to target OS X
- RSA4096 - first seen in 2015
- Petya - first seen in March 2016 and defeated in April 2016
In March 2016, Trustwave noted:
We are currently seeing extraordinarily huge volumes of JavaScript attachments being spammed out. Our Spam Research Database saw around 4 million malware spams in the last seven days, and the malware category as a whole accounted for 18% of total spam arriving at our spam traps.
Anatomy of Encrypting Ransomware
More often than not, ransomware is acquired by email. The payload can vary greatly, most common are .js, .doc, .xls, .rtf, .rar and .zip. The fact that it can be a .doc or .xls makes the email evade several spam filters.
Once the attachment is opened, the payload is executed[1], the real ransomware will be downloaded from the attacker's host. The ransomware will do a handshake with the attacker's host and agree on an encryption and decryption key.
The process will then start searching all files (even mapped network drives and offline cloud folders such as OneDrive and Dropbox) that match a long list of extensions, including videos, images, source code, bitcoin wallets and Microsoft Office files.
Some variants even go the extra mile and remove any Volume Snapshot Service (VSS) files, also known as shadow copies.
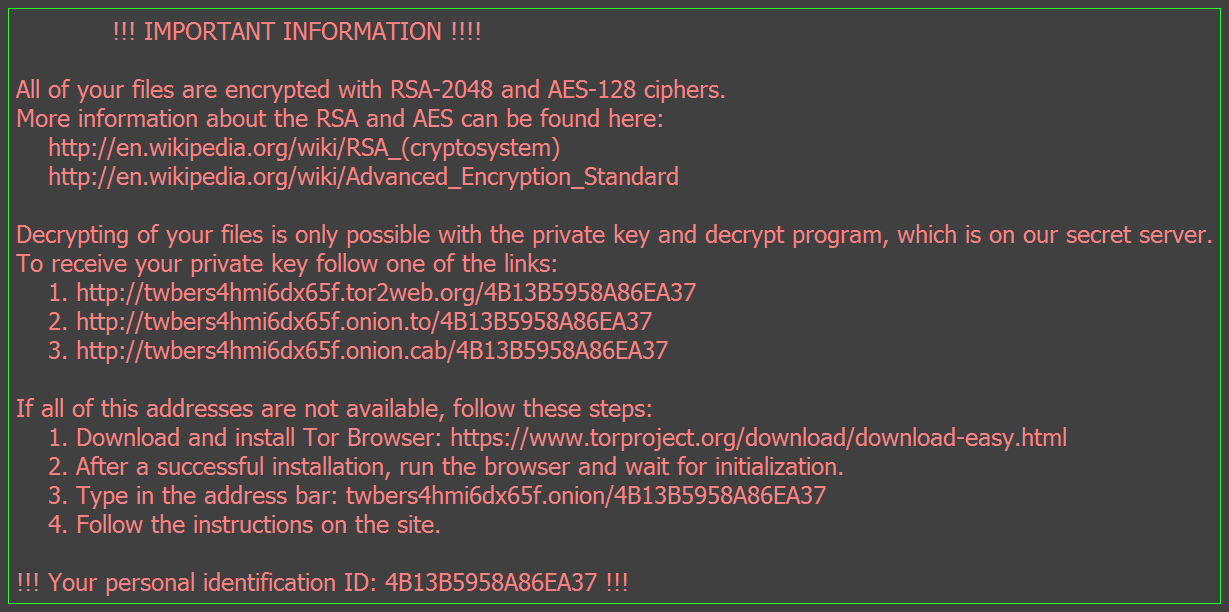
Once the encryption process is ready, you will be presented with the ransom message.
Mitigating Encrypting Ransomware
Unfortunately, there isn't a single thing that you can do in order to mitigate this kind of ransomware, especially in a zero-day. There are however some best practices you can use and deploy throughout your enterprise to help reduce your attack vector.
- Backups, Backups, Backups, Backups! Backups are the single best thing you can have to mitigate this kind of attack. You need to have a good backup policy which includes regularly updated backups. For more information on how to make a good backup policy, refer to my other blog post: Today is World Backup Day; don't be an April Fool!
- Filter your email attachments. Make sure that you block at least
.exe,.bat,.cmd,.scr,.vbs,.jsand.rtf. I also suggest you block.docand.xls. Yes, I know, these are Microsoft Office extensions, but you should move your enterprise to newer version of Office which support the more secure.docxand.xlsxfile formats. Ideally, you should also block.rar,.zipand.7z. Yes, users will complain, but email should not be used for file transfer. - Software Restriction Policies. Disable executables from running out of the
AppData,LocalAppDataor%tmpfolders. You can use the Ransomware Prevention Kit. This is a tool created by SMBKitchen Crew and Third Tier that automates the process of making a Group Policy to disable files running from the App Data and Local App Data folders, as well as disabling executable files from running from the Temp directory of various unzipping utilities. This tool is updated as new techniques are discovered for Cryptolocker, so you will want to check in periodically to make sure you have the latest version. If you need to create exemptions to these rules, they provide this document that explains that process. - File Server Resource Monitor. Actively monitor file shares. Write simple scripts that checks if files are being overwritten at an abnormal rate, or check for ransom notes. If you detect, kill the file share and alert the team.
- Permissions. Does everyone have read, write and execute access on every share? Use the Principle of Least Privilege.
- Antivirus. Yes, zero-days may often go undetected, and yes, the anti-virus may be dead, but at least it can act as a last line of defence if everything else fails. Teach your users to report virus alerts, not ignore them.
- Patches and Updates; early and often
- No Local Admin rights. I was a big believer in allowing users to have local admin rights on their workstations. Not anymore. Due to security reasons we had to remove this right, and I was against it. Until one of our users got a variant of a ransomware and it stopped it from removing shadow copies from the machine. I am a big believer in this now.
- Phish and train users. See if you can get users to open up phishing-like emails. Your security is only as good as your weakest link. Teach your weakest users and spread awareness across your enterprise on how to spot typical phishing indicators.
- Unplug from the network immediately. If you are suspicious of something, unplug it from the network immediately. If you act fast enough, you may stop the ransomware from making the handshake with the attackers servers. If you're not fast enough, at least you may stop the ransomware from encrypting your network shares.
- Never pay the ransom. First of all, these are criminals. They have no code of conduct. If you pay the ransom, there is no guarantee that you will get your data back. They will just steal your bitcoin. If people continue to pay these criminals, they will continue to extort users since their method works.
- Try some decrypters. If you are in desperate need of the data, you can try to identify which ransomware variant you have and try to decrypt the data. Ideally you should image your disk and try to recover everything from inside a VM. For example, if you have the Petya ransomware you can use the recovery method discussed here.
In the case of the legacy Word Documents it would execute a macro. ↩︎