Since last week I blogged about Protecting against Encrypting Ransomware, I thought it would be ideal to now talk about the announcement that @leo_and_stone was able to reverse engineer the hashing algortihm that is used by Petya.
Petya (also known as RANSOM_PETYA.A) is a new variant of ransomware, first seen in March 2016. It not only targets enterprise users, but also encrypts entire hard drives rather than just a selection of files. This ransomware has the ability to overwrite the affected system's master boot record (MBR) in order to lock users out.
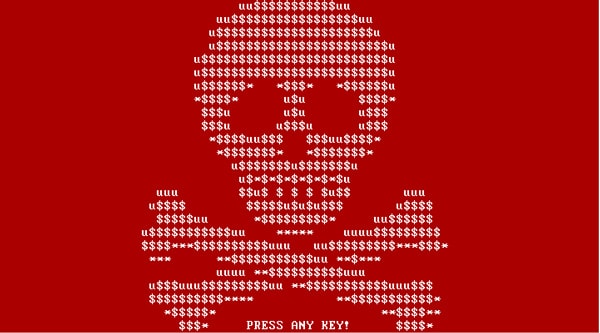
As soon as the MBR is overwritten, Windows will BSOD. The user will then reboot his PC and instead the modified MBR will load the Petya ASCII skull and a ransom message. Since the MBR is encrypted and a new MBR is set, the infected computer will not even be able to boot in Safe Mode.
Decrypting
If you are intersted in decrypting your Petya Encrypted Disk, you can visit his hosted app online here or via a mirror here.
To use this app you need to know the drive's verification data and nonce. The verification data is 512 bytes and located on the infected disk at sector 55 (0x37) offset 0(0x0). The nonce is 8 bytes and is located at sector 54 (0x36) offset 33(0x21).
An alternative (and easier way) to get this data is by connecting your infected disk to another computer and use Fabian Wosar's Petya Sector Extractor. When the Petya Sector Extractor detects the infected disk, you can copy the Sector and the Nonce and paste them in the decryption apps above.
The source code for reverse engineering the Petya is located on leo-stone's hack-petya GitHub repository.