HTTP Strict Transport Security (HSTS) is a web security policy mechanism which helps to protect websites against protocol downgrade attacks and cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should only interact with it using secure HTTPS connections, and never via the insecure HTTP protocol.
HSTS is an IETF standards track protocol and is specified in RFC 6797.
In short, HSTS is one of the best solutions available to avoid SSL stripping man in the middle attacks.
To implement HSTS, the server must supply the header Strict-Transport-Security over an HTTPS connection[1] to a User Agent. The max-age directive is the number of seconds after receiving the policy that the User Agent must treat the host as an HSTS host[1:1]. This directive is required. An additional directive that can be passed as part of the header is the includeSubDomains directive. This is optional, and if turned on instructs the User Agent to treat all subdomains of this domain as HSTS Hosts as well.
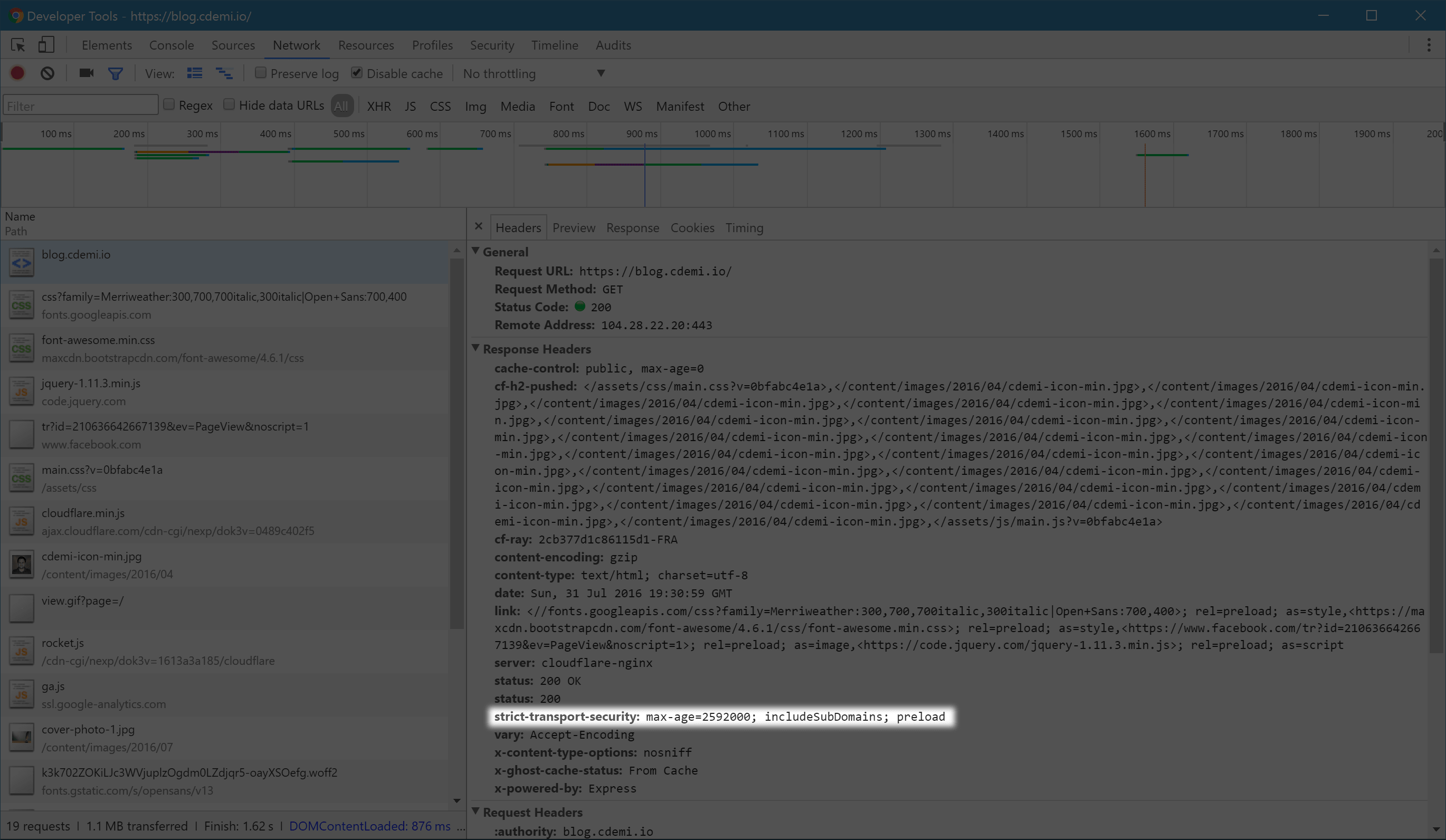
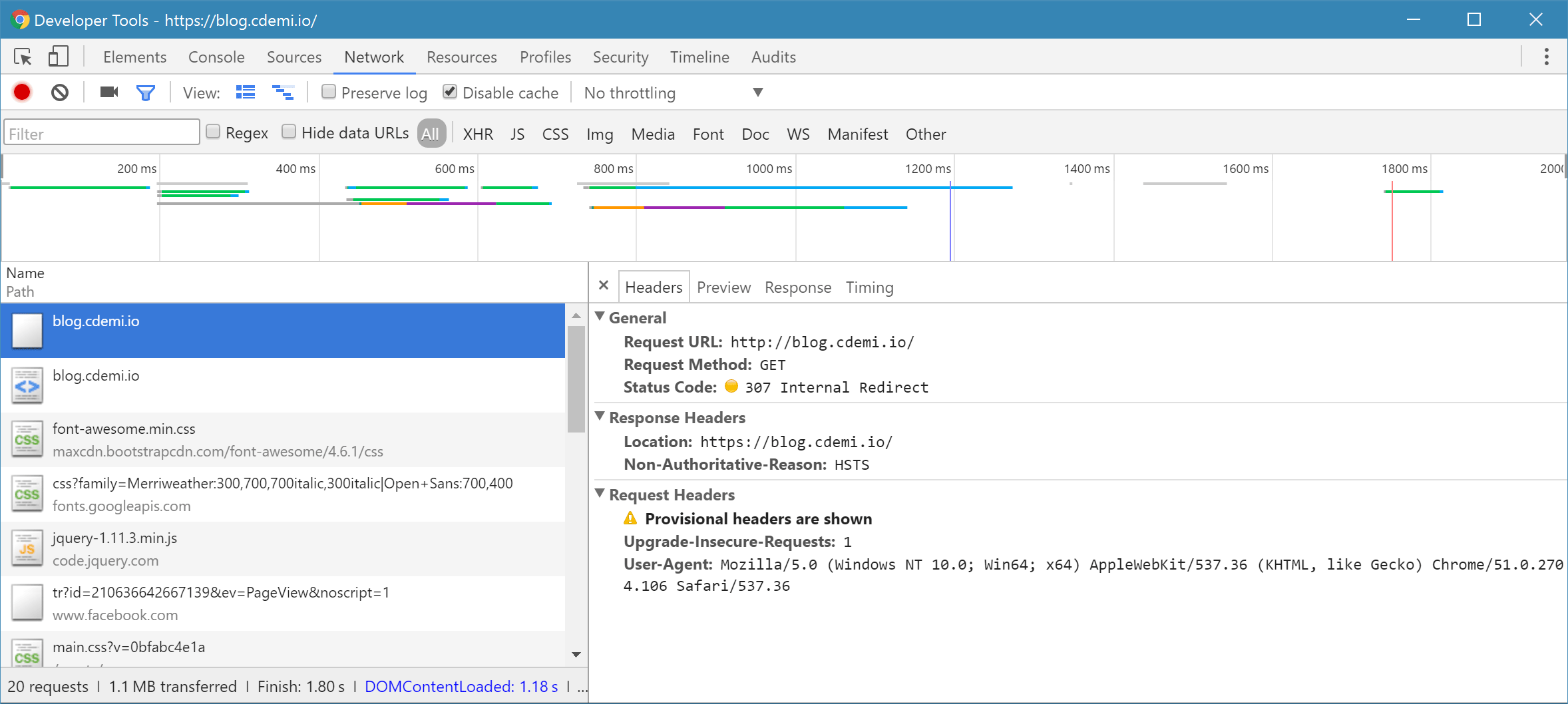
Once the User Agent gets an HSTS Policy (over HTTPS), he is required to observe the policy until the timeout of the max-age directive. This means that, as long as the HSTS Policy is active, any requests to HTTP to that domain, will not even be transmitted. The User Agent will upgrade the protocol to HTTPS before the first packet is even sent. In fact, we can see this even in the Chrome Developer Tools.
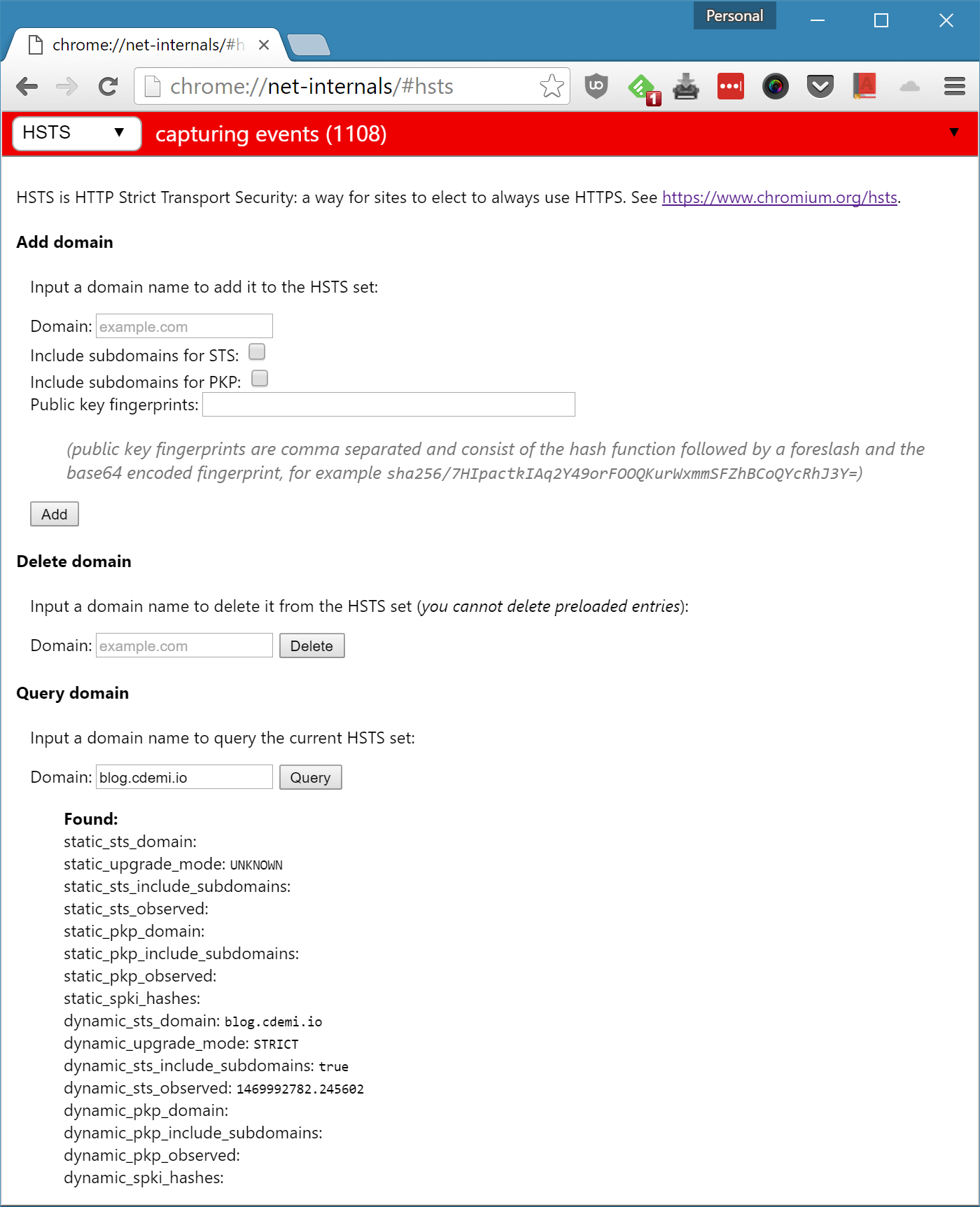
The Chrome Net-Internals HSTS Page chrome://net-internals/#hsts allows you to add, delete and query HSTS domains:
Preloaded HSTS List
The first time a User Agent is used, it wouldn't have information regarding HSTS status of any host. This would be the ideal time for a MITM attack since most probably the first request would be over HTTP.
Due to this, some browsers come preloaded with a list of HSTS hosts. We can have a look at the Chromium Source code src/net/http/transport_security_state_static.json.
If you own a site that you would like to see included in Chrome's HTTP Strict Transport Security (HSTS) preload list, you can submit it at https://hstspreload.appspot.com.
A max-age directive of 0 forces the User Agent to cease treating the host as an HSTS host. Refer to: The max-age Directive of RFC 6797 ↩︎ ↩︎