The Domain Name System Security Extensions (DNSSEC) (RFC 2535) is a suite of Internet Engineering Task Force (IETF) specifications for securing certain kinds of information provided by the Domain Name System (DNS) as used on Internet Protocol (IP) networks. It is a set of extensions to DNS which provide to DNS clients (resolvers) origin authentication of DNS data, authenticated denial of existence, and data integrity, but not availability or confidentiality.
RFC 3833 documents some of the known threats to the DNS and how DNSSEC responds to those threats. All answers from DNSSEC protected zones are digitally signed.
DNSSEC works by digitally signing records for DNS lookup using public-key cryptography. The correct DNSKEY record is authenticated via a chain of trust, starting with a set of verified public keys for the DNS root zone which is the trusted third party. DNSSEC was first deployed at the root level on July 15, 2010.
For example, here you can see, visualized, the chain of trust from the root zone to blog.cdemi.io:
In Windows Server
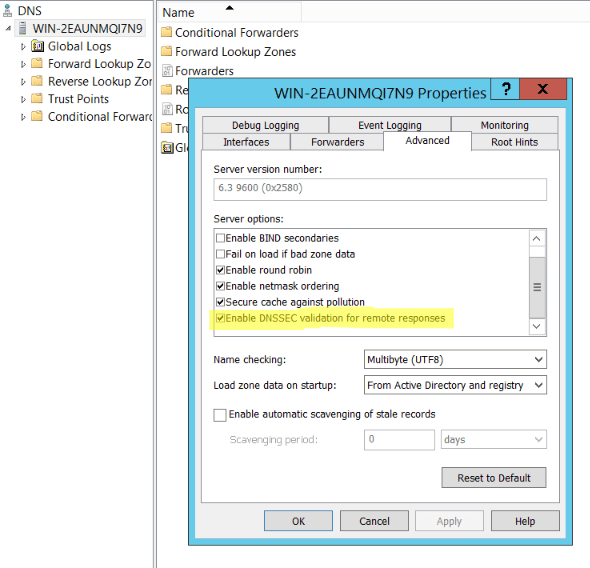
Fortunately, enabling DNSSEC Validation in Windows' DNS Server is fairly easy. First, we need to make sure that our DNS Server is configured to do DNSSEC Validation. We can do this by right clicking the DNS Server in the DNS Manager console and going in the advanced tab and selecting "Enable DNSSEC validation for remote responses":
Now that we have configured our DNS Server to validate DNSSEC we need to add a trust point. This is someone we trust, and who else better to trust than IANA's root anchor? This can be found at: https://www.iana.org/dnssec/files. This can be done in two ways:
Using dnscmd.exe
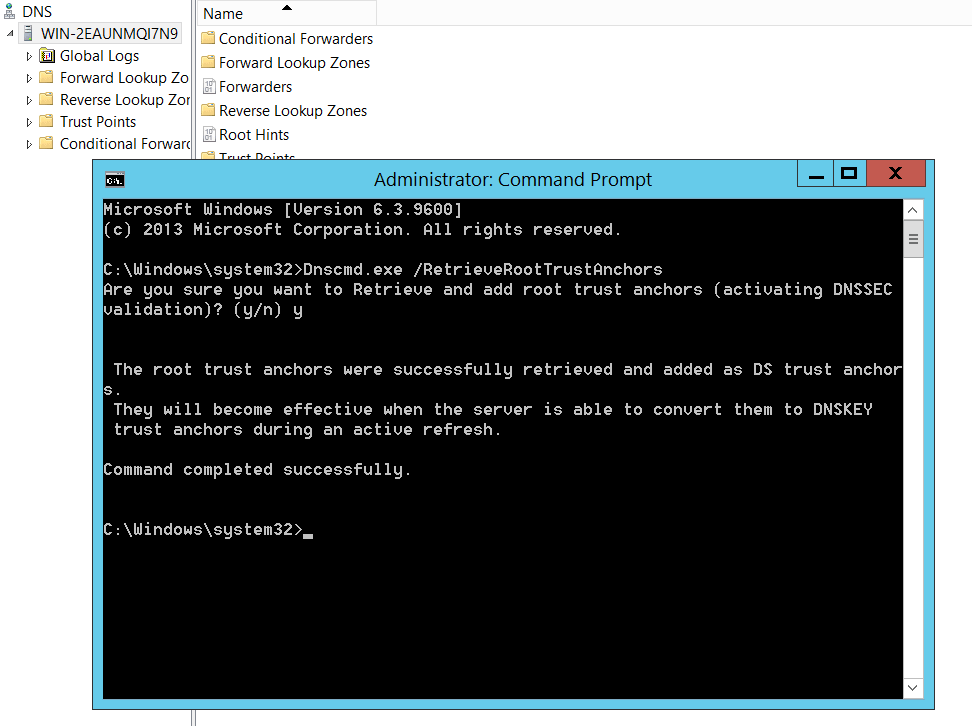
Conveniently for us, Microsoft has added a parameter to the dnscmd.exe to automatically retrieve the root trust anchors. From an elevated command prompt, you can run dnscmd.exe /RetrieveRootTrustAnchors.
Manually Importing
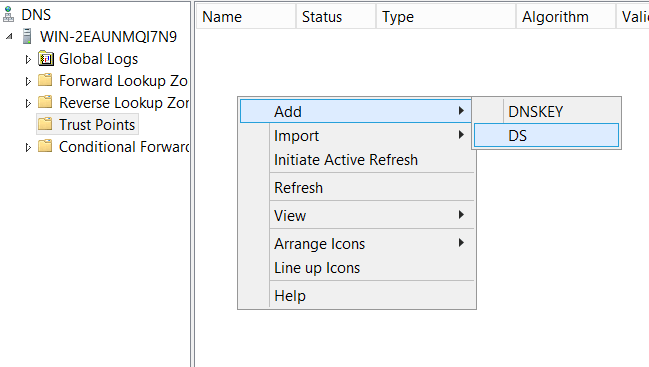
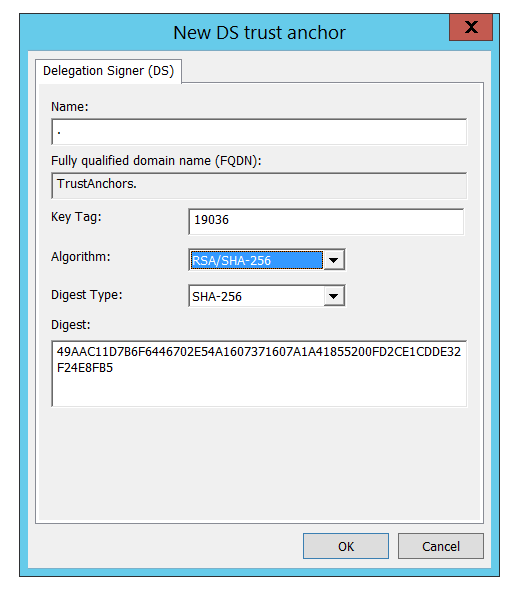
Alternatively, you can manually add a DS Key as your trust point. From the DNS Manager, we need to go to the Trust Points folder and Add a DS Key:
The DS Key can be found at https://data.iana.org/root-anchors/root-anchors.xml:
<?xml version="1.0" encoding="UTF-8"?>
<TrustAnchor id="AD42165F-3B1A-4778-8F42-D34A1D41FD93" source="http://data.iana.org/root-anchors/root-anchors.xml">
<Zone>.</Zone>
<KeyDigest id="Kjqmt7v" validFrom="2010-07-15T00:00:00+00:00">
<KeyTag>19036</KeyTag>
<Algorithm>8</Algorithm>
<DigestType>2</DigestType>
<Digest>
49AAC11D7B6F6446702E54A1607371607A1A41855200FD2CE1CDDE32F24E8FB5
</Digest>
</KeyDigest>
</TrustAnchor>
For convenience:
- Name:
. - Key Tag:
19036 - Algorithm:
RSA/SHA-256or8 - Digest Type:
SHA-256or2 - Digest:
49AAC11D7B6F6446702E54A1607371607A1A41855200FD2CE1CDDE32F24E8FB5
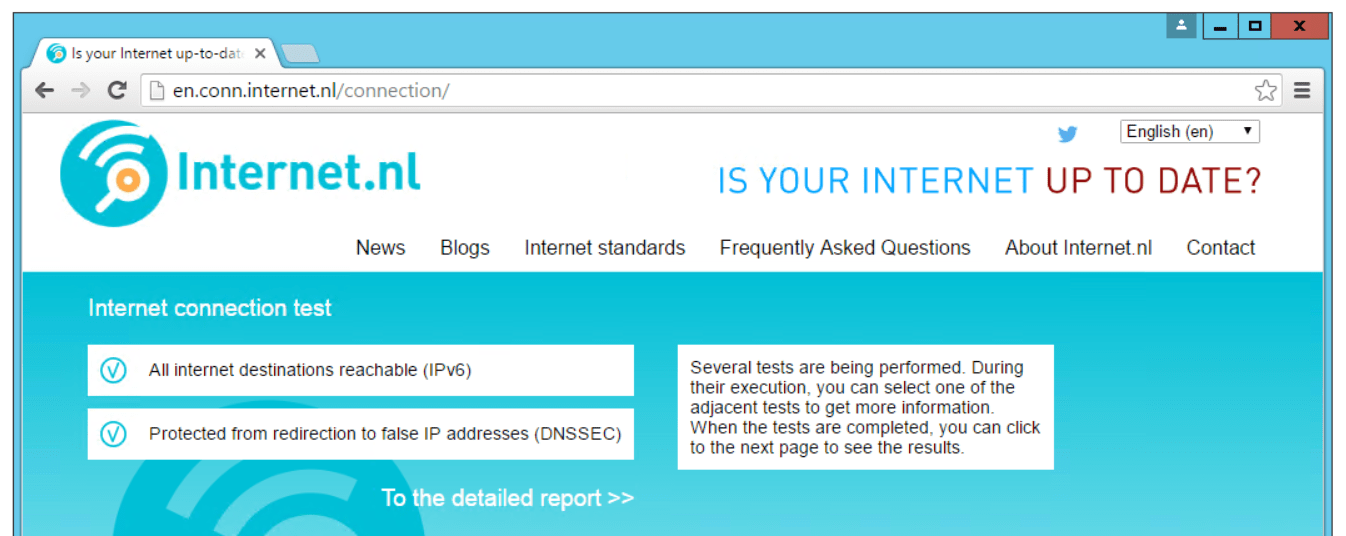
Testing that DNSSEC Validation Works
Hopefully, now, DNSSEC Validation through your Windows DNS Server is working correctly. Flush your DNS cache just in case and go to: http://en.conn.internet.nl/connection/. Hopefully you should see something like this: