Group Policy is a feature of an Active Directory environment where it provides a centralized management and configuration of operating systems, applications and users' settings. If you're a System/Network Administrator, you've surely used them to enforce a corporate security policy, and if you're a user, you've almost certainly been frustrated by the limitations imposed by these policies.
Unfortunately, there is one big problem with this, or rather with how organizations deploy their security infrastructure. If users in your Active Directory domain belong to the Local Administrators Group, they can get around these policies any time they want.
How?
In essence, policies are applied as follows:
This means that since the GPOs are applied last, they will be the ones overriding your Local Policy. The problem with this is that all policies, essentially, are changes to Registry Keys. This means that in order to bypass Active Directory Group Policy changes, all you need to do is to identify the policy's setting location and change it!
There are many group policy references available, but since machine group policy settings store in the HKEY_LOCAL_MACHINE branch of the Registry and per-user group policy settings store in HKEY_CURRENT_USER, if you don't know the location of the setting that's preventing you from doing something you want you can use RegMon (now replaced by Process Monitor) to find it.
Example
Restore Access to Removable Storage
For example, a very common policy applied is to Deny Access to Removable Storage as follows:
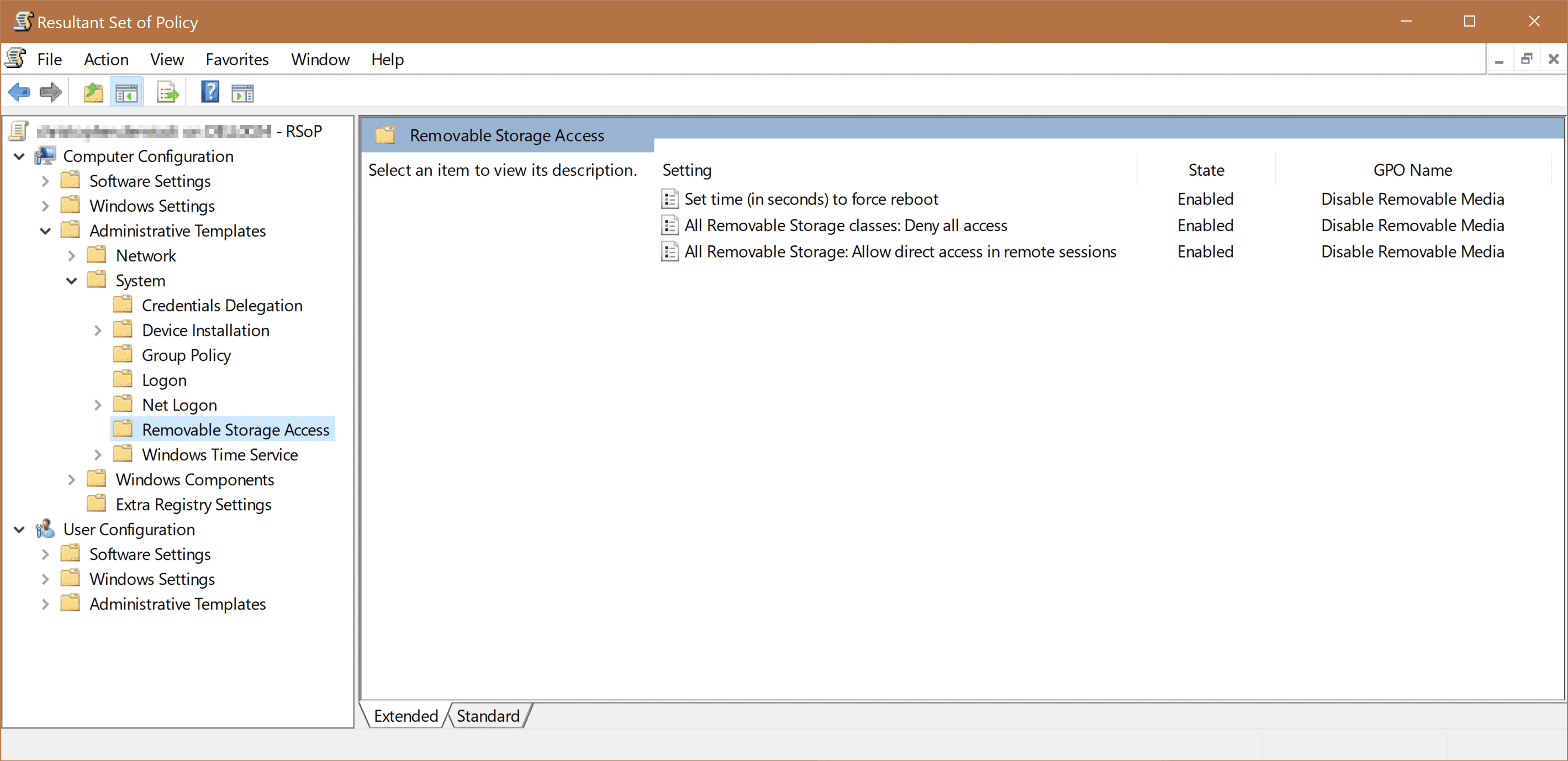
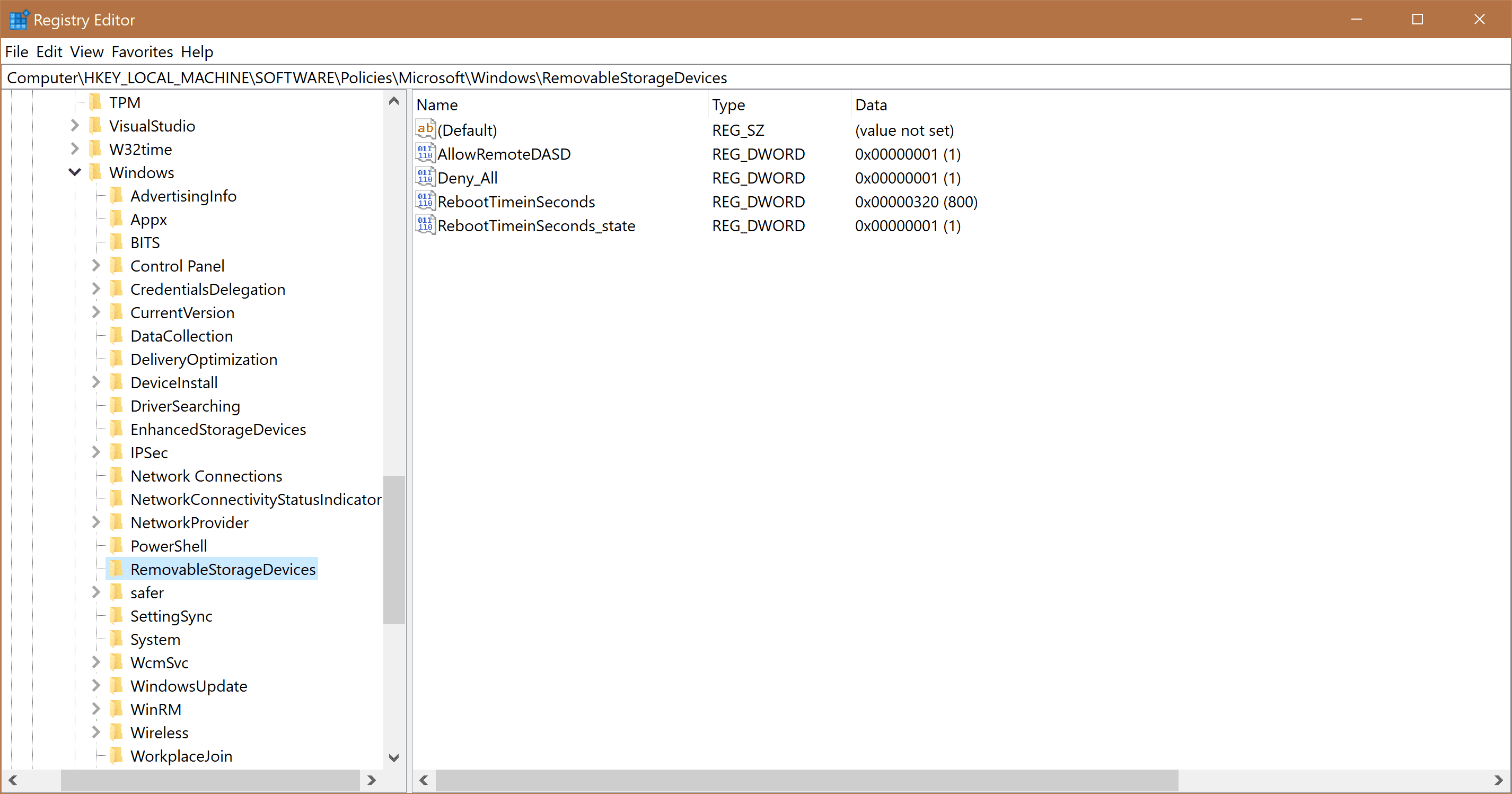
This means that as soon as this policy is applied, we should find equivalent Registry Keys showing this policy. In this case, we will find the Keys at Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\RemovableStorageDevices
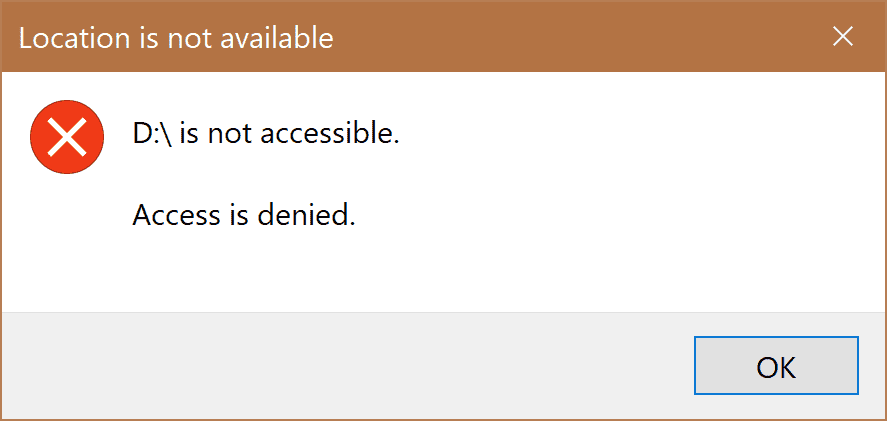
As expected, with this policy and registry keys, in place, the user can no longer access his Removable Storage devices.
So, in this case, all we need to do is just delete these Registry Keys and re-connect our removable storage. We can either do this manually or just run reg delete "HKLM\SOFTWARE\Policies\Microsoft\Windows\RemovableStorageDevices" /f in an elevated command prompt. Voilà, you can now access your removable storage again.
Skip Windows Server Update Services
Most of the times, system administrators in an organization point to their WSUS in order to reduce download bandwidth. Unfortunately, most of the time, these servers are never updated or the updates are not approved. In order to switch back to Microsoft's official update servers to have the latest security patches, you can just run in an elevated Command Prompt:
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU" /f /v UseWUServer /t REG_DWORD /d 0
net stop wuauserv
net start wuauserv
Conclusion
This blog post tries to highlight the fact that networks that run with users as local administrators have no way to enforce policies on their organization's computers. The reason that most networks leave their users with so much power is that many applications violate basic security programming guidelines and won't run otherwise.
