What is BGP?
BGP is, quite literally, the protocol that makes the internet work. BGP is short for Border Gateway Protocol and it is the routing protocol used to route traffic across the internet. Routing Protocols (such as BGP, OSPF, RIP, EIGRP, etc...) are designed to help routers advertise adjacent networks and since the internet is a network of networks, BGP helps to propagate these networks to all BGP Routers across the world.
BGP is defined by IETF in RFC 4271 and we are currently on version 4 (BGP4 or BGP-4) since 2006. BGP is a Layer 4 Protocol where peers have to be manually configured[1] to form a TCP connection and begin speaking BGP to exchange routing information.
How BGP Works
Autonomous Systems
Within the Internet, an autonomous system (AS) is a network controlled by a single entity typically an Internet Service Provider or a very large organization with independent connections to multiple networks.
These Autonomous Systems must have an officially registered autonomous system number (ASN), which they get from their Regional Internet Registry: AFRINIC, ARIN, APNIC, LACNIC or RIPE NCC.
A unique ASN (AS Number) is allocated to each AS for use in BGP routing. AS numbers are important because the ASN uniquely identifies each network on the Internet.
Peering
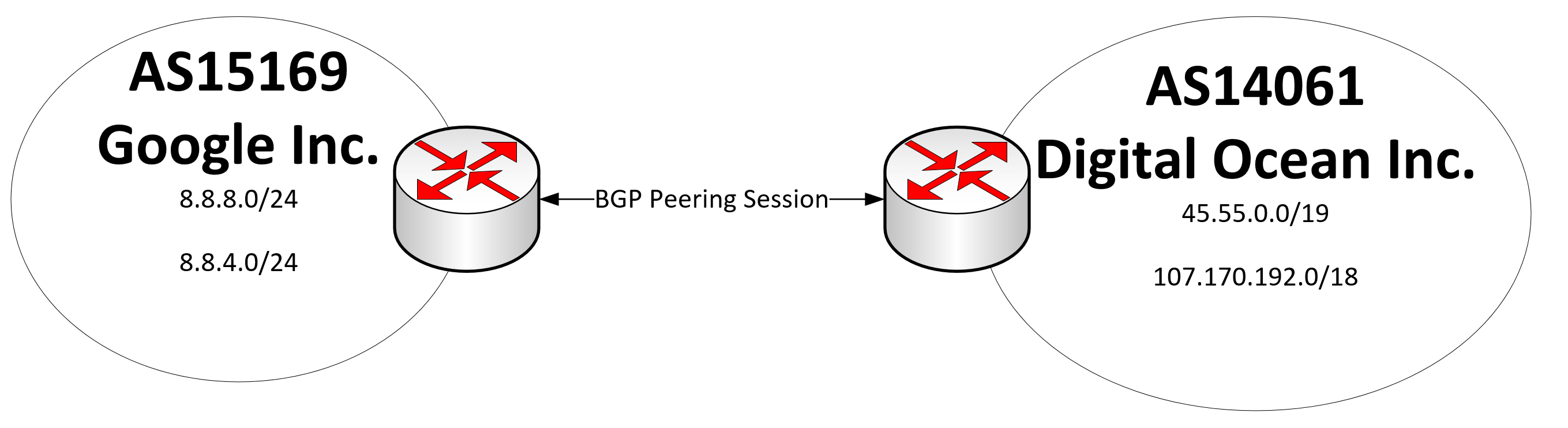
Two routers that have established connection for exchanging BGP information, are referred to as BGP peers. Such BGP peers exchange routing information between them via BGP sessions that run over TCP, which is a reliable, connection oriented & error free protocol.
Selecting the Best Path
Once the BGP Session is established, the routers can advertise a list of network routes that they have access to and will scrutinize them to find the route with the shortest path.
Of course, BGP does not make sense when you are connected only to one other peer (such as your ISP) because he is always going to be the best (and only path) to other networks. However, when you are connected to multiple networks at the same time, then certain paths will be shorter, faster or more reliable than others. For example, Google's AS15169 peers with 270 other networks (Autonomous Systems), one of which is Digital Ocean Inc. AS14061. They are both connected to other ISPs for the internet, however this way since they have now peered together, they can exchange routing information, so now their router can chose a shorter path of connectivity they have between themselves. If that neighbourship is broken for some reason or another, then their routers can re-arrange their routing tables to reach those Autonomous Systems through other Autonomous Systems such as Tier 1 ISPs like: Cogent (AS174), TeliaSonera (AS1299), Level 3 (AS1, AS3356, AS3549), NTT (AS2914), AT&T (AS7018), etc...
Misconfiguring or Abusing BGP
Since BGP is at the absolute core of the internet, when it is misconfigured or abused it can cause havoc across large portions of the internet.
For example, in 2008, when the Pakistan Government tried to ban YouTube, Pakistan Telecom (AS17557) used BGP to route YouTube's address block (AS36561) into a black hole. Accidentally (allegedly), this routing information somehow got transmitted to Pakistan Telecom's Upstream IP Transit Provider PCCW Global (AS3491) which then got propagated to the rest of the world. Most of YouTube's traffic from across the world ended up in a black hole in Pakistan. In this video, RIPE NCC Chief Scientist Daniel Karrenberg (@limbodan) uses BGPlay to replay the events in the BGP Routing Table during the YouTube outage.
Some other famous incidents are: AS7007 incident, Brazilian carrier leaks BGP table and Turkish ISP takes over the Internet.
Apart from misconfiguration, BGP can be also abused for malicious purposes. By taking advantage of unsecured BGP peerings or not verifying routes that are being announced from your peers, attackers may announce IP ranges that they do not actually own and thus routing internet traffic towards their links, essentially creating an MITM attack. For more information about this, I suggest you read Wired's Blog Post on Revealed: The Internet's Biggest Security Hole and the post from BGPmon: BGP Routing Incidents in 2014, malicious or not?
As businesses grow, however, they will start requiring BGP connectivity (any customer who wants to achieve truly redundant Internet access has to have its own AS and exchange BGP information with its ISPs), and you'll be forced to deploy BGP on more and more core and edge routers.
This short introduction to BGP should be enough for you to understand the basics of what BGP is and how it works, but it is by no means a good idea to operate it in a production environment until you have spent some time reading the RFCs.
There is no auto discovery in BGP. ↩︎